1 Introduction
Radio Frequency Identification (RFID) is a non-contact automatic identification technology that identifies and exchanges data by radio frequency. It is mainly used to identify a target in the RF area in a short period of time. When multiple electronic tags arrive at the RF active area at the same time, the tag will respond to the reader command and send a signal at the same time, causing the reader to not receive the data correctly, nor can the tag be correctly identified and conflicts occur. There is a need for a reliable anti-collision algorithm that solves the problem of data collisions that occur when multiple electronic tags are identified, causing the reader to fail to correctly identify the tags.
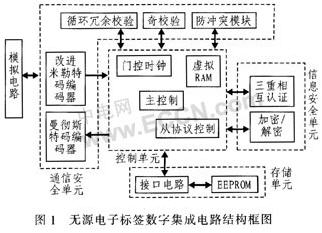
The block diagram of the passive electronic tag digital integrated circuit is shown in Figure 1. It consists of four units: communication security, information security, storage and control. The anti-collision module is located in the communication information security unit, and is used to solve the data conflict problem caused by data exchange between multiple tags and the reader.
2 ALOHA algorithm
The ALOHA algorithm is a simple anti-collision algorithm, as shown in Figure 2. It has neither a detection mechanism nor a recovery mechanism, but only ensures that the information sent by the electronic tag is accurately received by the reader with a certain probability. The ALOHA algorithm is only used for read-only readers. The tag transmits the data (serial number) to the reader and sends the data to the reader continuously in one cycle. The data transmission time is only a small part of the repetition time, so that in the transmission A fairly long pause is generated, so there is a probability that two transponders can transmit their data in different time slots, thereby avoiding collisions.
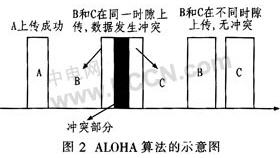
As can be seen from Figure 2, the reader first sends a read command, and multiple tags in the radio zone receive the command, and immediately select one of the subsequent multiple slots to upload the information to the reader, and the tag is cycled in one cycle. Complete data upload in the gap. Increasing the number of time slots can reduce the probability of collision of the RF terminal, but the channel will be in an idle state most of the time, making the anti-collision identification speed slower. Conversely, reducing the number of time slots leads to a significant increase in radio frequency terminal collisions. The key to using the slot algorithm is to find an effective compromise, so that the reliability and speed of anti-collision can meet the requirements. As the complexity of RFID systems increases, the reliability of anti-collision is significantly reduced, and conflicts are inevitable. Therefore, this anti-collision algorithm without detection recovery mechanism is only applicable to simple systems.
3 binary search anti-collision algorithm
Due to the inefficiency of the ALOHA algorithm, the actual RFID system is not used, but a more efficient binary search algorithm is adopted. The binary search algorithm is flexible and does not cause anti-collision failures. In the case of a collision of N transponders, only a N-1 anti-collision cycle is required to accurately identify a suitable transponder. The basic idea of ​​the binary search algorithm is that the reader determines the serial number of the transponder to generate a data collision location. The commander is then forced to send a message with a "0" or "1" in the conflicting position to exit the conflict. When N-1 transponders exit the post-conflict channel, they are completely occupied by the remaining transponders and recognized by the reader.
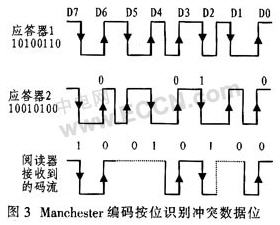
To prevent data collisions from occurring, first determine the specific location of the data bits in which the collision occurred. The Manchester code used here is shown in Figure 3. This code indicates high and low levels by the rising and falling edges of the level. The rising edge is logic "1" and the falling edge is logic "0". There is no case where the state is unchanged. Therefore, it is detected that the coding state does not jump during data transmission, and it is considered that a collision occurs during data transmission. The two conflicting data bits must have a logic "0" and a logic "1", so that the rising and falling edges of the Manchester code cancel each other out, so that the receiver receives the state for the duration. The subcarrier signal, that is, the state does not jump, which is not allowed in Manchester coding, it is certain that there is a conflict. This method can therefore be used to track the specific location of the conflicting data bits in bits.
Fruit Tools,Lemon Squeezer,Lemon Juice Squeezer,Pineapple Corer
Xiongyang Household Co., Ltd , https://www.yjkitchen-manage.com